The U.S. Cybersecurity and Infrastructure Security Agency (CISA), along with a coalition of U.S. and foreign security and law enforcement agencies, have released a list of the 15 most exploited vulnerabilities from 2021, calling on both public and private organizations to ensure these critical security bugs are mitigated and systems patched.
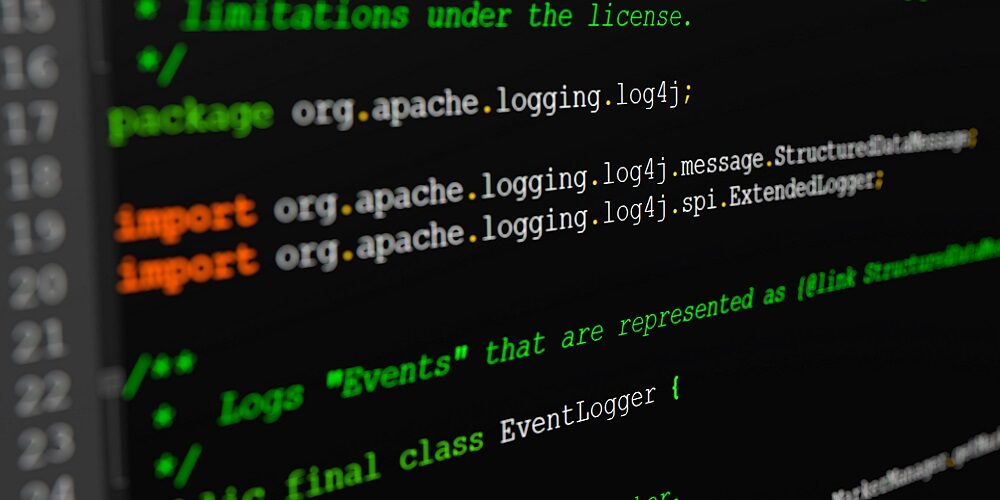
The list, published in a joint cybersecurity advisory between U.S., UK, Australian, Canadian and New Zealand agencies, includes many vulnerabilities IT professionals should already be familiar with, including Log4Shell, ProxyShell, ProxyLogon, ZeroLogon and other unnamed vulnerabilities impacting common IT products.
According to the advisory, agencies observed malicious actors routinely exploiting these vulnerabilities in 2021, and several of them were also routinely exploited in 2020, suggesting that the continued exploitation indicates that many organizations are still behind when it comes to patching software to protect against security vulnerabilities.
In fact, four of the top 15 most exploited vulnerabilities are at least two years old, including one each from 2019 and 2018.
Other bugs noted that didn’t make the top 15 include several from 2020 and prior, such as a pair of 2017 Microsoft Office remote code execution bugs and a remote arbitrary code execution bug in Cisco IOS and IOS XE. Others from 2021 include the Windows Print Spooler remote code execution bug known as PrintNightmare and flaws impacting products from VMWare, SonicWall, Accellion, Pulse Secure and others.
The advisory of the most exploited vulnerabilities from last year urges organizations to:
- Update their systems as soon as possible or implement vendor-approved workarounds.
- Use a centralized patch management system.
- Replace end-of-life software that is no longer supported by the vendor.
- Outsourcing patching and scanning to a cloud service provider or managed service provider in the case of limited IT manpower.
- Harden IT environments by introducing multi-factor authentication, regularly review privileged accounts, implement a policy of least privilege, configure networks securely, segment networks, monitor for malicious activity and more.
To learn about the 15 bugs listed, click “View slideshow” at the top left just above the main image, or here.
For more information on known exploited vulnerabilities, view CISA’s catalog of (as of April 28) more than 650 bugs that are being actively exploited.
If you enjoyed this article and want to receive more valuable industry content like this, click here to sign up for our digital newsletters!











Leave a Reply